The National Cyber Security Centre (NCSC) has issued a fresh warning over the dangers of using easily hackable passwords, ahead of National Pet Day, which falls on 11 April.... Read more »

The operators of Cring ransomware have been conducting a series of damaging attacks on industrial targets and control systems (ICS) after apparently acquiring a list of users of Fortinet’s... Read more »
Nation state-backed cyber attacks are becoming more widespread, varied and open than ever before, with the number of significant incidents doubling between 2017 and 2020, according to the University... Read more »
Facebook has attempted to deflect criticism of its data security practices while ducking calls to apologise for a leak of personally identifiable information (PII) on hundreds of millions of... Read more »

Hackers are targeting unpatched vulnerabilities in SAP applications, according to a report issued by SAP and cyber threat research company Onapsis. The report detailed more than 300 successful exploitations of critical... Read more »

A data leak of information on approximately 533 million Facebook users – including profile names, mobile numbers and location data – has prompted talk of regulatory action against the... Read more »

The enterprise definition of endpoint has dramatically shifted over the years. Endpoints traditionally referred to desktop computers and laptops, which could be secured with antivirus software and firewalls. Today,... Read more »

Here’s why cybersecurity incident response is something your entire organization has to care about: Hackers are likely trying to invade your network, and security vulnerabilities likely make this easier... Read more »
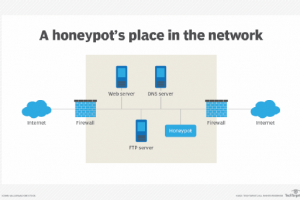
A honeypot is a network device that tricks hackers into thinking they’ve broken into an organization’s real network when actually they are in a fake network set up as... Read more »
The NHS is doing great work closing its security skills gap, with the average trust now employing twice as many in-house security practitioners – defined in this instance as... Read more »

