Introduction In modern commerce’s fast-paced, interconnected world, efficient motor carrier operations play a crucial role. They ensure the seamless transportation of goods from one point to another, serving... Read more »
In the shifting terrain of the business landscape, the importance of digital marketing, such as SEO and social media, has never been more pronounced. Driven by a focus on... Read more »
In 2023, a Hubspot survey found that 36% of marketers consider data to be crucial in effectively reaching their desired target audiences and gaining a deep understanding of their... Read more »
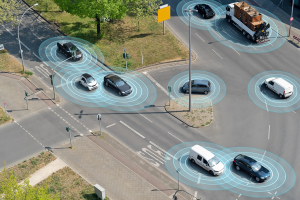
As many consumer electronics are actively undergoing an Internet of Things (IoT) revolution, other major sectors like the automotive industry have been slower to incorporate smart technology into their... Read more »
Data is everywhere. Look around; it is all data. It’s entrenched in almost every aspect of our lives, and it’s becoming increasingly important to organizations of all sizes. But... Read more »
By James Ovel, Operations VP at Zayo For a VP of Operations, commissioning, installing, and deploying a new subsea cable brings excitement and optimism, but equally offers significant challenges.... Read more »
Introduction In today’s rapidly changing business environment, agile data management and enterprise transformation are not just buzzwords; they’re crucial elements for organizations striving for sustainability and growth. However, when... Read more »
Introduction Enterprise system modernization-the phrase itself may seem daunting, but it’s an essential consideration for any business aiming to remain competitive in an increasingly digital world. However, moving from... Read more »
One of the biggest challenges organizations face is harnessing vast amounts of information from disparate data sources. The ability to harmonize this information is essential for making informed decisions,... Read more »
According to Google, 89% of the businesses say that anticipating needs and providing a great user experience is important for growth. The consumers of this digital era are more... Read more »

