Data Security Posture Management (DSPM) is the management of your cloud-hosted data to protect it from security risks and monitor it. This helps businesses understand what part of the... Read more »
Advancement in domain-specific industries with the unification of modern digitalization and the need to diversify for competitive advantage gain has elevated the need for developing software applications. The rapidness... Read more »
The business world increasingly relies on data, which has become a valuable asset for organizations of all sizes. So valuable that data security is no longer an ‘additional’ component... Read more »
Data has come to be regarded as an invaluable currency, and protecting sensitive information from falling into the wrong hands is an urgent imperative for organizations. In fact, with... Read more »
We’ve all been there: You’re running late for your flight, only to be met with a long line of passengers waiting for security checks. You brace yourself for the... Read more »
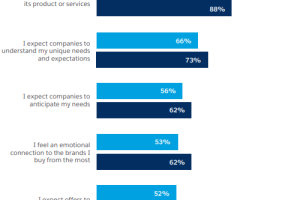
Advanced data analytics help businesses gain useful insights into their customers and industries to make data-driven decisions. Without data, you operate blindly and lose opportunities to impress your customers.... Read more »
Whether entering the cloud for the first time or being a clear veteran of the cloud in every way possible, the concern of security and responsibility remains. What is... Read more »
You may be wondering, how do I suppress my IP address? The most common method is through a residential proxy. A residential proxy is a method commonly used to... Read more »

