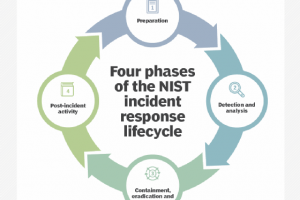
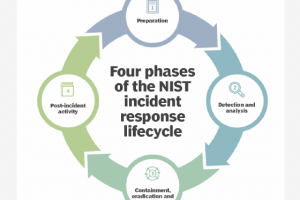
Incident response coordinates approaches to manage cyber incidents and fallout to limit the consequences. Incident response frameworks guide the direction and definition of response preparedness, planning and execution by... Read more »

Business email compromise has come a long way since its advent in the ’90s. Estranged relatives and Nigerian princes were ever in crisis; they needed money wired abroad —... Read more »

A CFO named Joe receives an email from CEO Taylor requesting a large payment to a contractor. In the email, Taylor stresses that the transfer is extremely time-sensitive and... Read more »
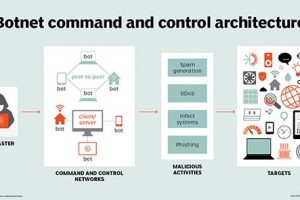
Although the terms security threat, security event and security incident are related, in the world of cybersecurity these information security threats have different meanings. A security threat is a... Read more »
CERT, CSIRT, CIRT and SOC are terms you’ll hear in the realm of incident response. In a nutshell, the first three are often used synonymously to describe teams focused... Read more »

Be careful where you click. Ransomware, like other varieties of malware, is commonly distributed via phishing emails. One wrong click on a malicious link or attachment can result in... Read more »

Ransomware attacks constituted 81% of financially motivated cyber attacks in 2020 and cost more in damages than any other malicious attack, according to a report from Atlas VPN. As... Read more »

Are you trying to sync your important files using OneDrive, only to experience an issue or bug? Do you want to learn how to fix OneDrive not working in... Read more »

A key fact to know about network penetration testing for beginners: If an organization pays someone to try to break into its network, it typically wants that person to... Read more »

The saying, “If it isn’t broken, don’t fix it,” doesn’t necessarily line up with the idea of network penetration testing, where a tester breaks into something typically to fix... Read more »

