
NetApp expanded Astra, its Kubernetes data management products, with a new software-defined storage service specifically focused on Kubernetes containers. The company introduced Astra Data Store, a scale-out, managed Kubernetes-native... Read more »

The BlackMatter ransomware gang has targeted US-based critical infrastructure entities, including two food and agriculture sector organisations, according to a joint cyber security advisory issued by US intelligence agencies.... Read more »

A “highly sophisticated” hacking group called LightBasin has harvested mobile network data from at least 13 telecoms companies in the past two years, according to CrowdStrike researchers. The group,... Read more »

Millions of people have begun heading back to the office after nearly two years of working from home. While the return of some office-based working is a positive sign... Read more »

The battle to win the headquarters of the UK’s National Cyber Force (NCF) has been quietly fought out of the public eye for the past 12 months. Samlesbury, in... Read more »

The issue of vulnerability management puts responsibility of varying natures and degrees across the organisation, including how, when and what to disclose (if anything) if the occasion arises. But... Read more »
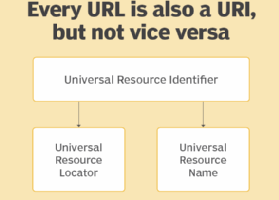
What is a Uniform Resource Identifier (URI)? A Uniform Resource Identifier (URI) is a character sequence that identifies a logical (abstract) or physical resource — usually, but not always,... Read more »

Home > Blog > Hygge: The Art of Making Your Home a Cozy Space The short days and long, dark nights. The frigid temps. The sheets of ice and... Read more »

The debate on what constitutes responsible disclosure has been running for some 20 years, with no end in sight. It’s not difficult to see why, with passionate researchers always... Read more »

Apple’s proposal to compel iPhone users to accept updates that would automatically and covertly search shared images for possible abuse material and send reports to Apple or law enforcement... Read more »

