
Up to and possibly more than 50% of Microsoft Exchange servers located in the UK appear to be vulnerable to three distinct vulnerabilities that were patched some time ago,... Read more »

With a global surge in ransomware attacks, governments have concentrated their attention on what drives these attacks’ popularity among cyber criminals. Most have concluded that it is their profitability.... Read more »

A public backlash against NHS Digital’s General Practice Data for Planning and Research (GPDPR) data-sharing plan saw more than a million people exercise their right to opt out of... Read more »

Civil society groups have called for a ban on the use of life facial-recognition (LFR) technology amid claims that the government and the police are introducing intrusive surveillance measures... Read more »
Looking at log files generated by IT infrastructure software is one of the less exciting parts of an IT administrator’s job, but those log files determine the health of... Read more »
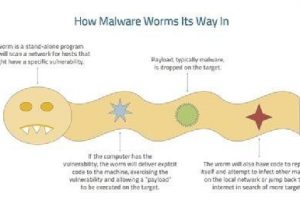
What is the ILOVEYOU virus? The ILOVEYOU virus comes in an email with “ILOVEYOU” in the subject line and contains an attachment that, when opened, results in the message... Read more »
Sweden’s leading IT and telecoms companies anticipate a robust negative economic response by China following the administrative court’s (Förvaltningsrätt) decision to uphold a ban on the use of technology... Read more »
We all know data privacy does not exist in isolation. It is not a solitary indication of an enterprise’s morality and compliance, separated from the operations and lifeblood of... Read more »
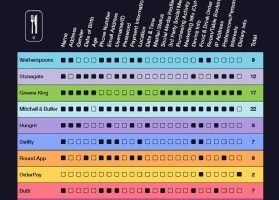
Food and beverage-ordering apps run by Mitchells & Butlers, the company behind chains such as All Bar One, Browns and Harvester, as well as pubco Greene King, have emerged... Read more »
Almost three-quarters of IT executives are concerned that the trickle-down of cyber attack tactics, techniques and procedures (TTPs) used by nation state-backed actors will impact their business, according to... Read more »

