Ransomware attacks are expected to grow both in frequency and effectiveness in 2021, with researchers at Cybersecurity Ventures predicting attacks to occur every 11 seconds and ultimately cost victims... Read more »

Modern security strategies should take an inside-out approach, not outside-in. “Understanding how to protect assets inside the security perimeter is far more important than focusing on preventing attackers from... Read more »
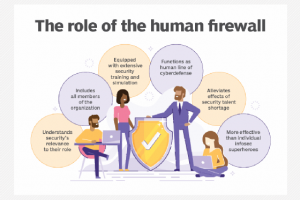
The proliferation of cybersecurity breaches is forcing government and business leaders to analyze the limitations of technology and reevaluate the role of people. Despite incredible advances in both threat... Read more »
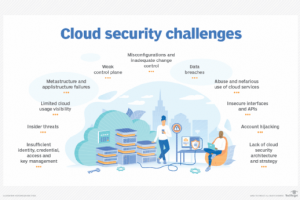
All the major promises of the cloud — improved IT efficiency, flexibility and scalability — come with one major challenge: security. Many organizations can’t delineate where cloud service provider... Read more »

One of the more popular cybersecurity trends in 2021 will undoubtedly be Secure Access Service Edge, or SASE. As enterprise networks evolve to better manage traffic from remote employees,... Read more »
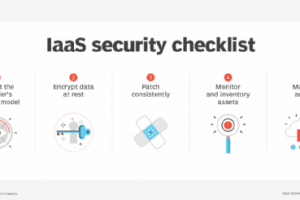
Many organizations have almost completely replaced virtual data centers, on-premises servers and appliances with IaaS. This widespread implementation requires a mobilization to secure IaaS environments to match this increased... Read more »
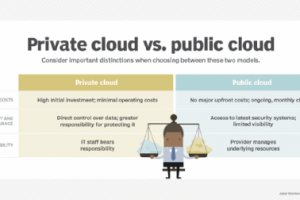
Regardless of whether an enterprise’s infrastructure operates in a private, public or hybrid cloud, cybersecurity is a critical component. While some cloud architectures greatly simplify security tasks and tool... Read more »

By Published: 21 Jan 2021 Organizations using cloud technology to support operations must follow good security practices. Establishing cloud security policies is key to achieving this. In short, a... Read more »

The importance of identity and access management in the modern digital enterprise cannot be denied. These programs ensure employees have timely access to the resources needed to complete their... Read more »

Endpoint detection and response tools protect organizations’ endpoints by monitoring for suspicious behavior and collecting system activities and events. Many are equipped to automatically respond to threats, such as... Read more »

