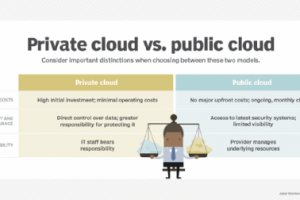
Regardless of whether an enterprise’s infrastructure operates in a private, public or hybrid cloud, cybersecurity is a critical component. While some cloud architectures greatly simplify security tasks and tool... Read more »

By Published: 21 Jan 2021 Organizations using cloud technology to support operations must follow good security practices. Establishing cloud security policies is key to achieving this. In short, a... Read more »

The importance of identity and access management in the modern digital enterprise cannot be denied. These programs ensure employees have timely access to the resources needed to complete their... Read more »

Endpoint detection and response tools protect organizations’ endpoints by monitoring for suspicious behavior and collecting system activities and events. Many are equipped to automatically respond to threats, such as... Read more »
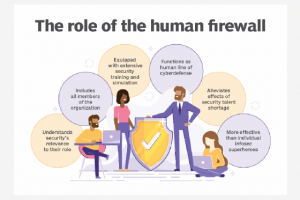
Businesses must prioritize cybersecurity now more than ever. This process requires a broader scope than investing heavily in security technologies, however — the tactic most companies have relied on... Read more »

Many 2020 cybersecurity predictions were thrown out of orbit when coronavirus cases emerged and COVID-19 was declared a global pandemic by the World Health Organization in March. This year,... Read more »

Konstantin Emelyanov – Fotolia By Today’s security teams are under immense pressure, faced with having to secure the rapid, widespread adoption of IoT in the enterprise. Factor in the... Read more »
Share It’s hard to get any work done when you’re surrounded by papers on your desk, or even your countertops and tables. Whether they’re cluttered with newspapers, bills, or... Read more »

By Published: 09 Dec 2020 One of the most prevalent technologies used in security operations centers today is the SIEM platform. However, SOC teams are struggling to adapt on-premises... Read more »
Google Play has announced the winners of its year-end awards, including users’ and editors’ picks for the best apps, movies, TV shows and books. As has been the case... Read more »

