The creation and use of portable, digital vaccine passports risks endangering basic rights, and could easily result in a situation where everyday activities such as browsing in a shop... Read more »

As the rate of cybersecurity incidents grows, security teams are looking for all the help they can get to prevent, detect and respond to attacks. Many organizations are understaffed... Read more »

What Is Cloud Computing? We live in a world where new technological advancements are brought about to solve problems in an easy, fast, and efficient manner. In a society... Read more »
Cyber attacks are one of the biggest threats facing organizations today, particularly during the COVID-19 pandemic. A large contingent of the workforce now works from home, new devices are... Read more »

When it comes to developing a comprehensive cybersecurity strategy, no single architecture type or product can protect against all threats. Instead, an assortment of security tools must be deployed... Read more »
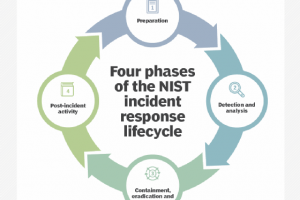
Incident response coordinates approaches to manage cyber incidents and fallout to limit the consequences. Incident response frameworks guide the direction and definition of response preparedness, planning and execution by... Read more »

Business email compromise has come a long way since its advent in the ’90s. Estranged relatives and Nigerian princes were ever in crisis; they needed money wired abroad —... Read more »

A CFO named Joe receives an email from CEO Taylor requesting a large payment to a contractor. In the email, Taylor stresses that the transfer is extremely time-sensitive and... Read more »
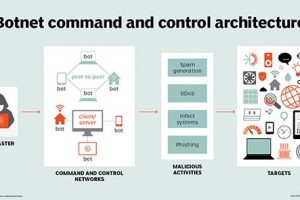
Although the terms security threat, security event and security incident are related, in the world of cybersecurity these information security threats have different meanings. A security threat is a... Read more »
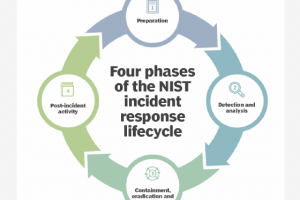
CERT, CSIRT, CIRT and SOC are terms you’ll hear in the realm of incident response. In a nutshell, the first three are often used synonymously to describe teams focused... Read more »

