Anyone who has ever heard of the so-called dark web has also probably heard of the Tor network, or The Onion Router project. However, there’s another decentralized network that’s been around for just as long, called Invisible Internet Project, or I2P for short. This begs the question: what’s the difference between I2P vs Tor?
Key Takeaways: Tor vs I2P
- I2P and Tor are both decentralized and anonymous peer-to-peer networks.
- I2P is more secure than Tor, but generally can’t be used to access the regular internet outside of services like email, chat and torrenting
- Both Tor and I2P let you access the deep web. With I2P these are the only websites you can access, whereas Tor can be used as a regular browser as well.
The shortest answer is that the two networks have different use-cases and different ways of anonymizing your traffic. Tor is mostly focused on accessing the regular internet anonymously, whereas I2P serves more as its own separate network, closer to what you might consider a dark or deep web.
Both Tor and I2P can be difficult concepts to wrap your head around, so we’ll start by outlining why you might want to use either of them in the first place.
-
Yes, I2P is undoubtedly more secure than Tor, as it doesn’t rely on potentially compromised exit nodes run by volunteers. However, it’s less useful for browsing the regular internet.
-
Tor is only as anonymous as the exit nodes and traffic allows. If you’re sending already encrypted traffic over Tor (such as by using a VPN), then Tor is anonymous and will make it even harder for someone to trace your traffic. That said, a malicious exit node can see any unencrypted traffic you send, and even alter it to include malware.
I2P vs Tor: Why Should You Hide Your Internet Traffic?
There are many reasons to use networks like I2P and Tor, but because the networks operate very differently, they’re not identical.
Why Use Tor (The Onion Routing Project)
Although Tor is mostly famous for providing access to the deep web, this is not its main intended use-case.
While this is possible, and Tor-only websites do exist (known as onion addresses), the main reason to use Tor is to access the regular internet (or “clearnet”) with a greater degree of anonymity. However, doing so without some other type of protection (like a VPN) can still be risky, as we’ll talk more about later.
Why Use I2P (Invisible Internet Project)
Contrary to the Tor network, the reason you’d want to use I2P is almost entirely to access websites or applications specifically designed to run on the network. This ranges from communication and messaging applications that need to be completely anonymous, to online black markets and piracy sites.
Another area where I2P excels is torrenting, as there are BitTorrent clients (such as Vuze) that make torrents from the regular internet available over I2P.
What Is Tor?
Now that we know what the two networks are for, it’s time to take a look at how they actually work, starting with Tor.
Applications configured to use Tor go through a process known as “onion routing” to route your traffic through three separate “nodes” before it reaches its destination (i.e. the website you want to access). These nodes are Tor routers (known as an onion router) that are set up and maintained by volunteers that contribute the resources to the network.
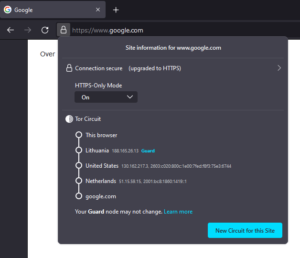
This is where Tor’s inherent weakness enters the picture. The final node in the chain is known as the “exit node,” and whoever runs it has the ability to potentially see and tamper with your internet traffic. This is because your traffic is encrypted as you send it to the first node, but the final exit node needs to decrypt it again to send it to its final destination.
What Is I2P?
Now that we have a working understanding of Tor, we can move on to I2P, which, despite having been around for just as long, is far less popular than its sibling. Where Tor is relatively easy to set up and even has its own pre-configured browser (known as the Tor Browser), I2P is a lot more complex and requires more tweaking from the user, which explains its relative lack of popularity.
Like Tor, I2P is a decentralized anonymous network that allows for peer-to-peer communication. Unlike Tor, it doesn’t rely on volunteer-maintained nodes, but instead every router on the network is turned into a node capable of relaying traffic for other users. This makes it far more decentralized, which protects I2P from things that can cripple the Tor network, like DDoS attacks.

I2P’s Strengths
Because Tor operates on a limited number of volunteer nodes operated by a small number of Tor users, it will always be vulnerable to DDoS attacks, as an attacker can target known nodes with excessive amounts of traffic to cripple or shut them down. With I2P, this isn’t possible, as every device that connects to the network inherently strengthens the network itself.
It also means that I2P isn’t vulnerable to the same weakness of malicious exit nodes. Since every single router connected to the network is a node, it discourages malicious actors from attempting to set up nodes to capture or alter traffic. Since every single device that connects to the I2P network has to be a node, it’s not an efficient vector for attacks.
Although it’s technically possible to use an I2P connection to browse the regular internet, there are very few exit nodes, and the ones that exist are often quickly taken down. That means that I2P is a much more closed loop than Tor is, with the exception of torrents. Several torrent clients essentially act as a bridge for torrents from the clearnet so that they can be downloaded over I2P.
The fact that it’s such a closed loop is another thing that works in I2P’s favor, privacy-wise. Because there’s no exit node to the regular internet, the final layer of encryption isn’t peeled away before the package has reached its recipient, further lowering the impact and risk of malicious nodes.
What Makes I2P and Tor Different?
We’ve already covered some of the differences between I2P and Tor, both in terms of how they route traffic across nodes and what they’re primarily used for. In order to truly understand the difference, though, it’s necessary to look at the underlying routing process used by both networks, namely Onion Routing and Garlic Routing.
Onion Routing vs Garlic Routing
Onion routing is the technique used by Tor, and essentially describes a process where multiple layers of encryption are added to a message (like an onion), which are then “peeled” away one at a time by each node, resulting in a decrypted message at the destination.
In theory, this ensures that no one in between the sender and the exit-node is able to see the contents of the message. However, one significant weakness of this approach is that it’s still vulnerable to something called “timing analysis,” where an attacker is able to compare the time and size of messages across devices to connect them together.
For example, say you are sending a message over Tor to another person. Your ISP may not know what’s in the message. However, if it keeps a log of all your traffic, the ISP can use that to cross-reference and know that the anonymous traffic left your device and went to the other person, because the time and size of the package match.
Garlic routing is the solution to this problem. Instead of sending messages individually like in onion routing, garlic routing bundles multiple messages together.
These messages pass through the I2P nodes before being exposed at the end point and sent to their individual delivery addresses. This makes it much harder to perform traffic analysis on an individual, as all their packages are bundled with that of other people and applications.
I2P and Tor vs VPN
At the end of the day, you’ll want to use a virtual private network if you want to stay anonymous while browsing the regular internet. Tor can be an additional layer of protection, but without a VPN you might just as easily be exposing yourself to more breaches of privacy than you would have faced unprotected.
Because of that, you shouldn’t consider using Tor for anything without also connecting to a VPN. NordVPN comes with built-in onion routing and is the best VPN for Tor, followed by ExpressVPN and Surfshark (read our full NordVPN review).
As for I2P, using a VPN in conjunction with it isn’t as useful. The more decentralized nature of I2P combined with garlic routing means that it’s not a security risk to use it without a VPN. However, your internet service provider can still tell that you’re using the I2P network for something, even though it has no idea what for, so use a VPN if you want to avoid that.
Final Thoughts: I2P and Tor Network
In many ways, I2P is simply a better and more secure version of Tor. It fixes the more famous network’s biggest weaknesses, such as malicious exit nodes, reliance on volunteers, DDoS attacks and timing analysis. However, it’s also less usable than Tor, with it being restricted to applications and websites designed specifically for I2P.
This limits I2P usage to things like email, torrenting, IRC and the deep web, but for these purposes it’s about as anonymous as you could possibly make yourself. Tor, on the other hand, has a much wider array of use-cases, but comes with so many flaws that you’re better off just using a VPN, or at the very least in conjunction with a VPN.
That’s it for our simplified explanation of Tor vs I2P. Do you feel like you have a better grasp of what these terms mean, or are you no less confused than you were when you got here? Have you ever used Tor or I2P for anything before? Let us know in the comments below, and as always, thank you for reading.
The post I2P vs Tor: Online Anonymity Explained & Compared for 2023 appeared first on Cloudwards.

